Additional Contributor: Pradnya Padaki
Stepping into a Security Operations Centre (SOC) at Cisco Live Melbourne for the first time was an experience charged with excitement and slightly nervous. Previously, my only understanding of SOCs came from listening to customer stories and handling their challenges—I had known the pressure, urgency, and teamwork required only through their eyes, never having been in those shoes myself.
Onboarding: Quick and Welcoming
Contrary to my expectations of a drawn-out onboarding, the process was surprisingly swift (taking less than 10-20 minutes). Thanks to Duo, I was quickly given access to all the essential tools: Cisco XDR, Splunk, firewall dashboards, and more from the duo directory. This seamless entry calmed my nerves and made me feel instantly welcome.
After that, it was all about getting comfortable with the tools and escalation processes. As a Tier 1/Tier 2 analyst, my daily routine revolved around Cisco XDR, which brought together incident alerts from every corner of the network. Each alert came packed with context and intelligence, making investigations much less overwhelming.
Discovering Endace
One of my highlights was using Endace for the first time. This tool gave me the ability to dive into packet-level details, filter data rapidly, and transition from high-level incidents to granular packet captures. Correlating metadata and network flows became straightforward and even enjoyable, helping me solve problems with much more confidence.
Candid Conversations
During the event, I was frequently put on the spot to share my firsthand experience of working in a SOC for the first time, particularly reflecting on my day two investigations. This encouraged me to observe carefully and think deeply about the operational realities. Many customers showed keen interest, recognizing that my experience could soon mirror their own, which made these interactions especially valuable and motivating.
Day 1: Learning the Ropes
The first day was all about orientation: understanding the workflow, getting to know the tools, and developing the mindset needed for effective investigations. With support from experienced colleagues, I learned to triage incidents, check threat intel, dive into logs, and consult with the team before making decisions. By the day’s end, my initial nervousness had transformed into excitement.
Day 2: Leading My Own Investigation
On day two, I took on incidents independently, performing full triage and drafting escalation reports myself.
Case Study: Investigating Suspicious Network Connections
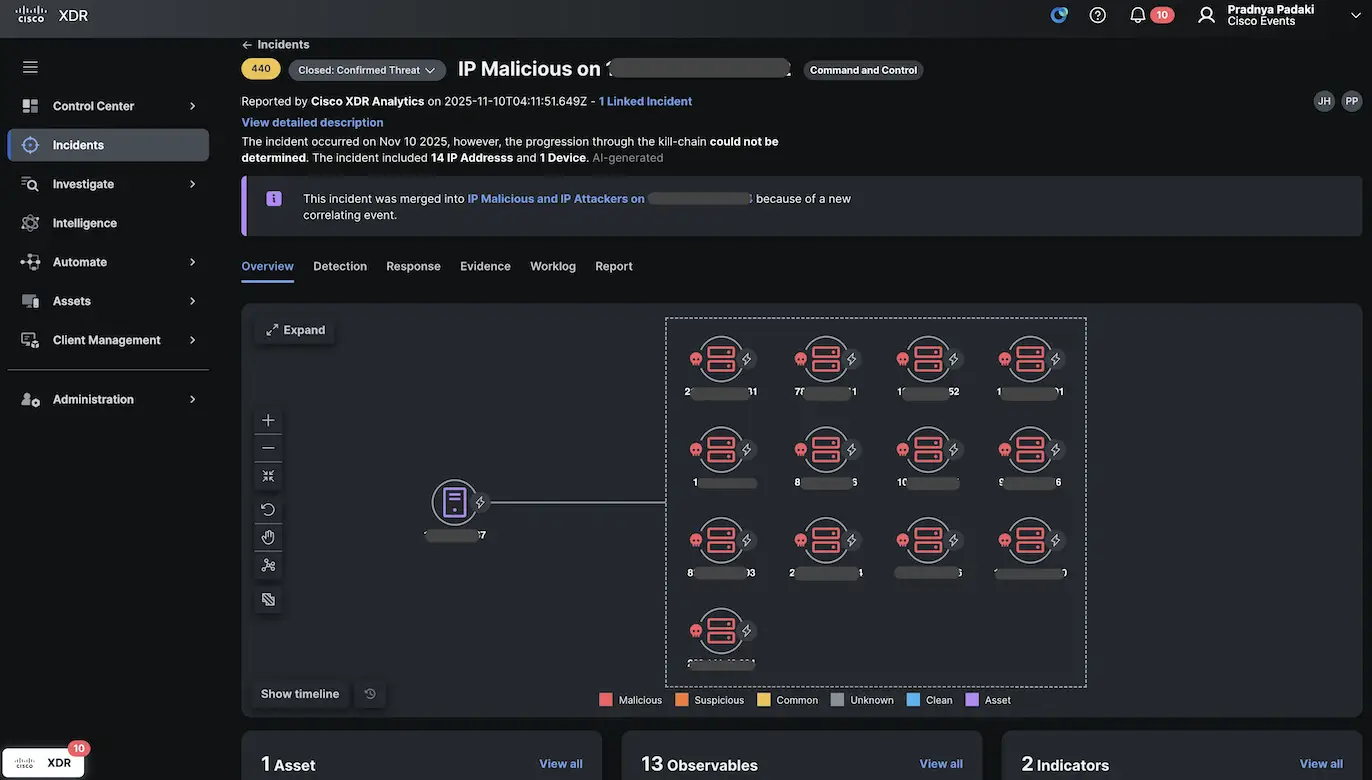
Background: During my initial SOC assignment, an alert was generated by Cisco XDR highlighting that an internal endpoint was making connections to multiple IP addresses known for malicious activity.
Detection: Cisco XDR flagged the suspicious behavior, visualizing the connections between one internal asset and several high-risk external hosts. This raised immediate concerns about potential malware or command-and-control activity (see Cisco XDR investigation below).

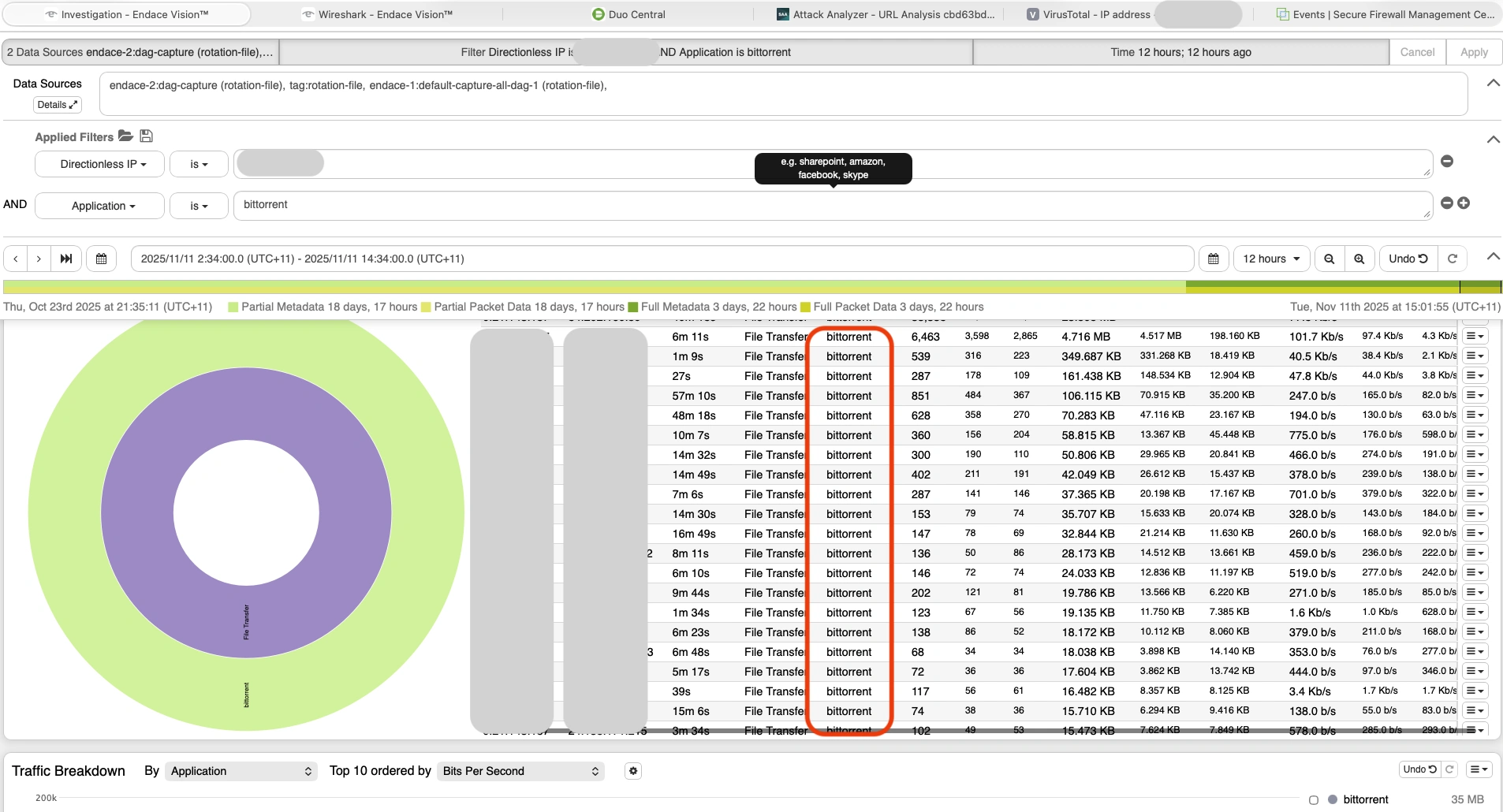
Investigation: To validate and further analyze the incident, I used Endace for in-depth packet inspection. Filtering for the specific IP and application revealed a consistent flow of traffic matching file transfer patterns. Further analysis confirmed that the traffic was generated by a BitTorrent application operating on the endpoint (see Endace screenshot below).

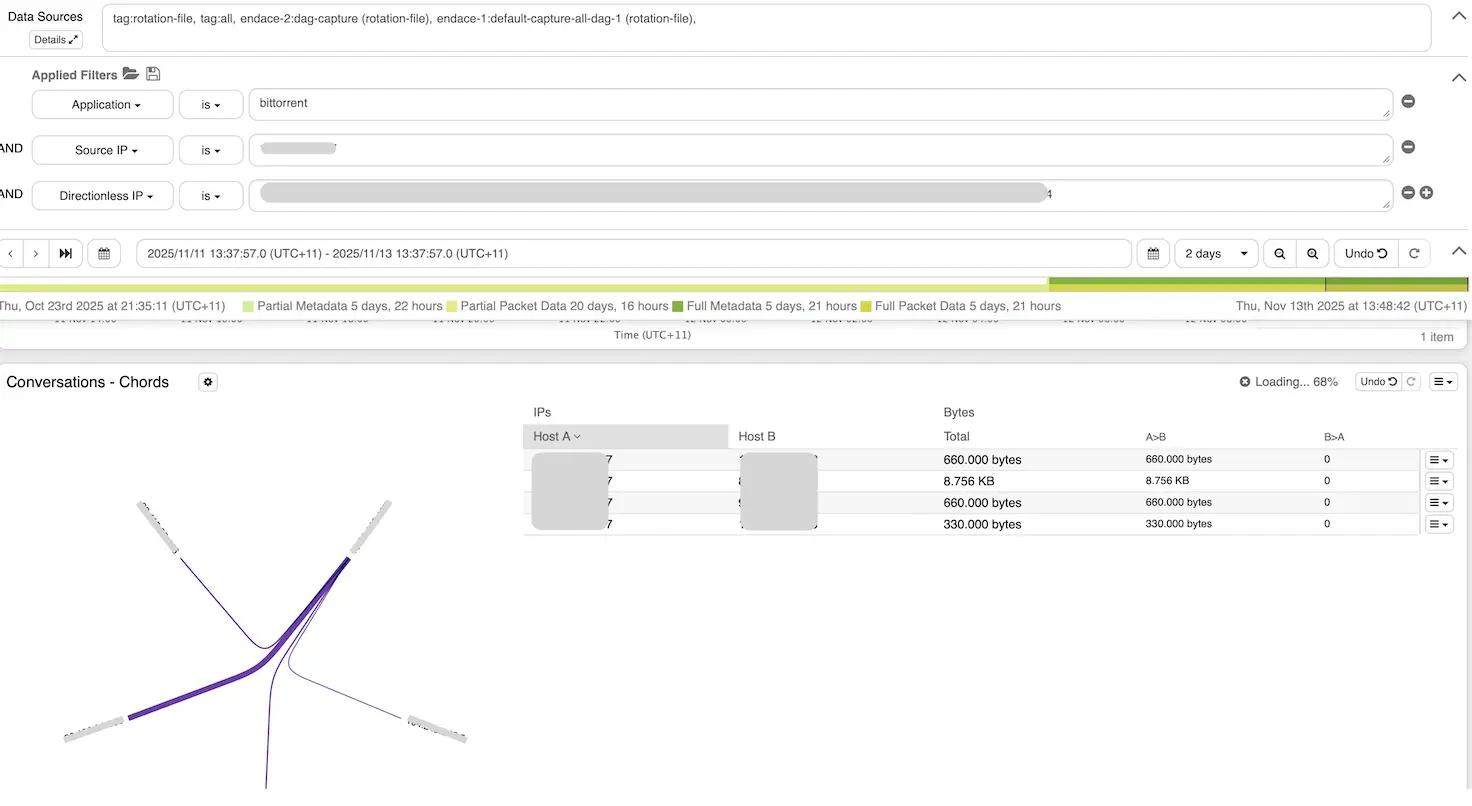

Response action: From the first alert in Cisco XDR, I performed a comprehensive investigation to quickly verify the violation of policies. As a Tier 2 analyst, my response included correlating data from multiple sources, conducting packet captures with Endace to rule out malware, and assessing the broader impact on the environment. Once the investigation confirmed Bittorrent usage as the source of suspicious traffic, the case was formally escalated to ensure appropriate follow-up, including user education and enhanced network controls to mitigate recurrence. The affected endpoint was flagged for further monitoring, and the application was disabled to prevent ongoing peer-to-peer file sharing. A detailed incident report was compiled, outlining risks such as malware exposure, bandwidth consumption, and privacy vulnerabilities associated with unauthorized Bittorrent activity.
Outcome & Reflection: Seeing the investigation through initial alert to root cause determination—leveraging both Cisco XDR and Endace—marked a major milestone in my SOC journey. This end-to-end incident handling not only reinforced procedural discipline but significantly boosted my confidence in handling real-world threats.
Reflections and Takeaways
By the end of the event, I realized the real essence of a SOC isn’t just about tools or dashboards. It’s about people: collaboration, trust, shared curiosity, and supporting each other. Even as a newcomer, I was welcomed, trusted, and encouraged—which made a world of difference.
In summary, my first SOC experience turned initial nerves into genuine confidence. I entered as an observer and left feeling like part of the team—a journey defined by support, learning, and the thrill of solving real-world security challenges.
Check out the other blogs by my colleagues in the Cisco Live Melbourne 2026 SOC.
We’d love to hear what you think! Ask a question and stay connected with Cisco Security on social media.
Cisco Security Social Media












